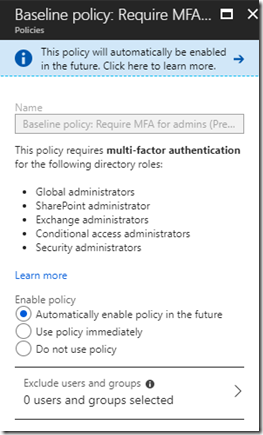
I’ve been working on conditional access for a while now with a client, trying to find the right balance of command and control versus usability for the organisation. Just as I thought we were there, I noticed a new policy called “Baseline policy: Require MFA for admins (Preview)” had appeared. Given that this is buried in the Azure Portal, I don’t think a lot of Office 365 admins will be aware of this just yet!
I hadn’t added this, neither had my client, so I clicked into the policy for more information and took a look at the configuration pane for this policy.
The link at the top takes you to a link explaining what Baseline Protection is. Basically it’s a set of predefined conditional access policies. Given that there is currently only one policy, I think we’ll see Microsoft creating a few more of these over the coming months. (I’d actually like to see them bring a lot more control over things like Risky sign-ins into the cheaper license skus, but this is a good start!)
In this case, when the policy is enabled, it will automatically enforce MFA on anyone who is in the directory roles listed in the policy window. This is great, unless your users have their day to day accounts configured for MFA, in which case they’ll need to sign-on using MFA, even when logged into a trusted device on the company LAN. That’s not actually as bad as it sounds as by default you can select a “don’t ask me for MFA on this device for X number of days”, where X is configurable between 0 and 60 in the MFA settings.
Personally, I think this is a great move and most companies should consider enabling this policy immediately, but make sure you warn your admins first and I would advise that you get them to visit https://aka.ms/MFASetup in advance of this to get their authenticator app configures as soon as possible as this makes signing on a breeze, just requiring you to click “Approve” on the authenticator pop-up (Even easier if you’re wearing a smart watch too!)
One thing that the link does call out, is if you’re using privileged accounts in your scripts these will be affected by the policy. You can exclude those accounts from the process but the link suggests using App Service Principals instead. I must admit I haven’t tried these yet when accessing Office 365 resources, but I aim to do that very soon and will post here a guide on how to use them.
Paul.